Resilience: Internal Services and External Access
Or how to keep services running even when the world (and your main provider) goes down
Today, almost every organization has internal services that, for various reasons, need to be accessible externally: email, telephony, VPN, information exchange services, etc. This raises a logical question - what happens if the internet simply disappears?
Of course, working without electricity or internet is challenging. But it's even worse when your provider is operational, yet your services are inaccessible because they're tied to a specific IP address, a single provider, a single route. If that provider fails, you vanish from the Internet.
I'd like to share a real-life case and some ideas on how to enhance resilience without spending thousands of dollars monthly.
The Problem: One Provider — One IP Address
The weakest link is the public IP address through which the world accesses your services. If this address is provided by only one provider, your reliability equals that of the provider. In my case, the main provider suddenly stopped working one morning due to technical issues, causing us to lose:
- External access to email
- Part of IP telephony
- Integration and information exchange services with partners
- VPN for remote employees
Everything that could fail - did. The reason: dependence on a single IP address from one provider.
Of course, the provider eventually recovered. After this incident, we developed an action plan for such cases. Naturally, once services were restored, we asked ourselves, "What can we do to prevent this from happening again?" Spoiler: unfortunately, there are no simple solutions.
Solution #1: Own Autonomous System (AS)
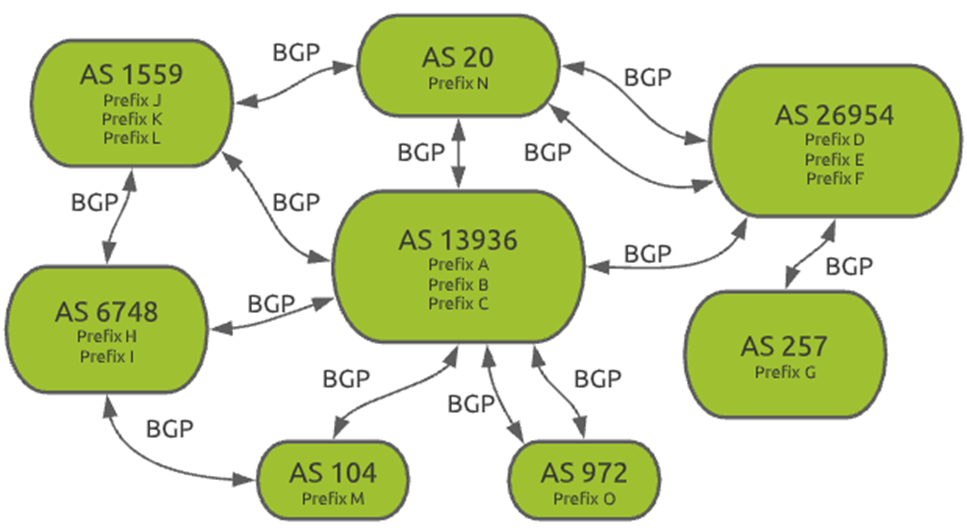
Having your own AS is like having your own registration in the internet. You obtain a pool of IP addresses and announce to the world via BGP (Internet routing decision protocol): "I'm accessible through these providers." If one fails, another remains.
Advantages:
- Maximum resilience and autonomy
- Availability remains even with significant degradation of external connections
- Your IPs stay with you, regardless of the provider
Disadvantages:
- Requires knowledge of network stack, BGP, router configuration
- Not all providers agree to connect external AS
Solution #2: Multiple Providers – "Budget" Redundancy
A basic option is to connect additional providers. In our case:
- ISP 1 – main channel
- ISP 2 – backup, but with unstable reliability
- Starlink for Business – as a "last resort," but satellite internet has its own issues
It seems simple - manually switch the IP address and continue working. However, each provider has a different IP address, and services don't "adapt" quickly, or the process takes a lot of time. Automatic switching in such cases is either very complex or impossible.
Conclusion: Manual mode works. Automatic mode - only if you put in significant effort or have your own AS.
Solution #3: Proxy or NAT via Data Center
Another option is to move the gateway or proxy server to the cloud/data center.
Scenario:
- Internally, services operate as usual
- Externally, everything goes through a tunnel to the cloud (VPN, GRE, WireGuard)
- In the cloud or data center – a public IP where your email, SIP, VPN, services, etc., "live"
Advantages:
- No need to have an AS
- Any functioning channel can be used to connect to the cloud
- High resilience if tunnels are well configured
Disadvantages:
- Latency if the data center is poorly chosen
- Tunnels need to be maintained continuously
- Dependence on a partner data center or cloud (they can also fail)
Conclusion
Ensuring the resilience of internal services is not a luxury but a necessity for stable business operations. The optimal solution depends on your infrastructure specifics, budget, and technical capabilities. The best approach is to combine several strategies to provide maximum flexibility and reliability.